Cyber security is the technique of securing computers, electronic systems, networks, and data from online malicious attacks. It is also known as Information technology security. It focuses on keeping cybercriminals and malicious hackers from gaining access, disrupting, or changing the systems and applications without the owner's consent. Cyber security in Nepal started its peak in 2017 when 58 different governmental sites were hacked by a group of hackers named “Paradox Cyber Ghost”. They leaked the customers' information and citizens' information creating a threat to the general public as well as governmental organizations.
Because an organization’s assets are composed of a variety of different platforms, a strong cyber security posture requires coordinated efforts across all of its systems.
What is the importance of Cyber security in Nepal?
Cyber security in Nepal is important to protect personal, government data, information and server from theft, damage, and malware. Without cybersecurity, neither an organization nor an individual will be able to defend their data from cyber-attacks. The level of cybercrimes is increasing day by day and becoming more vulnerable. Many innocent users get affected by cybercrimes through different cyber-attacks that are attempted by hackers. It has become as risky in the present world as the world is digitizing and technologies are developing and more hackers are evolving and inventing new ideas to attempt cybercrime.
Due to the increasing number of cybercrimes, cyber security in Nepal is very important and a greater necessity to keep personal and confidential data, information safe. Different organizations are implementing cyber security to protect confidential data and information and to protect servers and networks. One of the great information security scandals to be remembered was the 2019 Facebook record breaking 5 billion dollar fine which Facebook agreed to pay to the US Federal Trade Commission. At the highest levels of government and business, the need to protect confidential information is a top priority.
Related: Reasons to study IT in Nepal
What are the cyber security issues in Nepal?
Some of the major cybersecurity issues reported in Nepal include ransom, phishing, and data breach, banking frauds, defamation, slander, online identity theft and individual cybercrimes.
In June 2017, a group of Turkish hackers hacked the Department of Passport Official website leaving a threat to reveal government's data. In October, the Swift system of NIC Asia bank was hacked by an unidentified hacker. Similarly in April 2020, data of more than 160,000 customers of Vianet Communication were leaked through twitter handles. Due to this act, various companies have started to provide dynamic cyber security services to help businesses and organizations cope with data breaches.
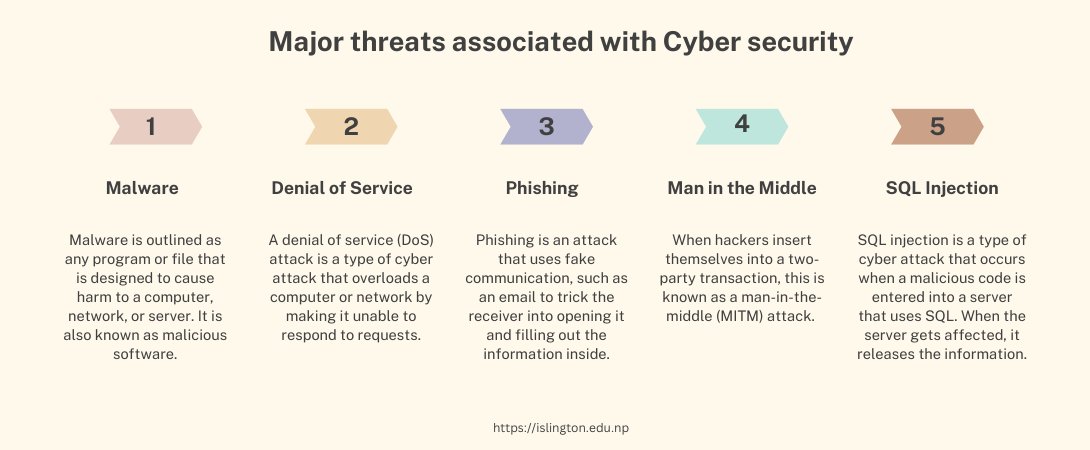
Major threats associated with Cyber security
Cyber security threats are attacks that menace and put information in danger. It is an attempt to unlawfully gain access to networks and accounts without the owner's consent, steal confidential information, or corrupt data. The various cyber security threats are:
-
Malware:
Malware is outlined as any program or file that is designed to cause harm to a computer, network, or server. It is also known as malicious software. It is activated when a user clicks on a malicious link or attachment.
-
Denial of Service:
A denial of service (DoS) attack is a type of cyber-attack that overloads a computer or network by making it unable to respond to requests. A distributed denial of service (DDoS) attack accomplishes the same thing, but the attack originates on a computer network.
-
Phishing:
Phishing is an attack that uses fake communication, such as an email to trick the receiver into opening it and filling out the information inside (such as providing a credit card number, password, etc.)
According to Cisco, "the goal is to steal sensitive data such as credit card and login information or to install malware on the victim's machine."
-
Man in the Middle:
When hackers insert themselves into a two-party transaction, this is known as a man-in-the-middle (MITM) attack. According to Cisco, after interfering with traffic, they can filter and steal data. MITM attacks are common when a visitor connects to an unsecured public Wi-Fi network. Attackers place themselves between the visitor and the network, then use malware to install software and manipulate data.
-
SQL injection:
SQL injection is a type of cyber-attack that occurs when a malicious code is entered into a server that uses SQL. When the server gets affected, it releases the information. A website's search box is used to submit vulnerable malicious code with ease.
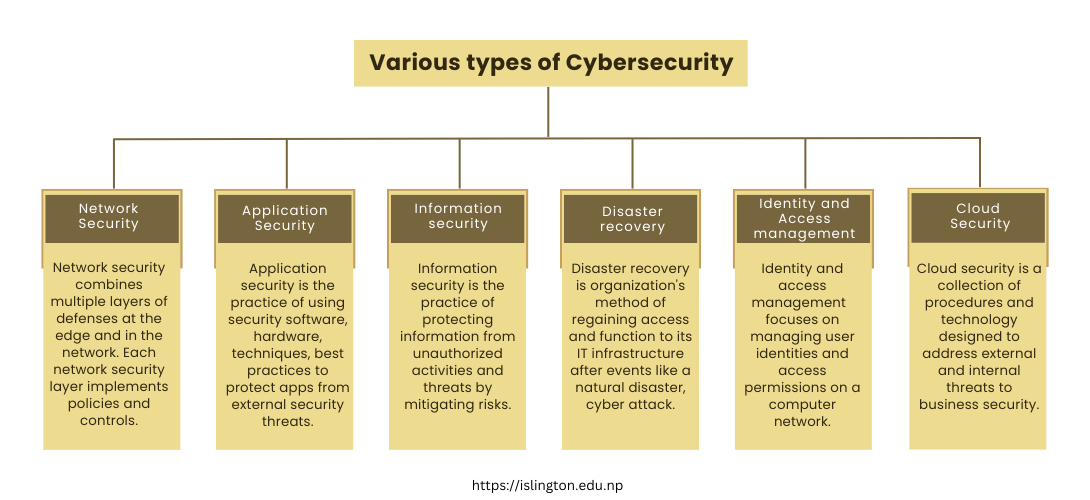
Various types of Cybersecurity
Knowing the various cybersecurity domains is also essential for preparing you for the knowledge requirements if you decide to work in the industry.
-
Network security:
Network security is one domain that helps secure a computer network from intruders like attackers or malware. There is the implementation of both hardware and software techniques to secure the network from unwanted access, disruptions, and misuse.
-
Application security:
Application security focuses on keeping software and devices free from threats. There is the installation of various defenses within the software of an organization to protect data against a wide variety of threats.
-
Information security:
Data integrity and privacy are protected by information security in both storage and transit. Application software helps in keeping the information safe and secured.
-
Disaster recovery:
Disaster recovery and business continuity define how an organization responds to a cyber-security incident or any other event that causes the loss of operations or data. Disaster recovery policies dictate how the organization restores its operations and information to return to the same operating capacity as before the event.
Business continuity is the plan the organization falls back on while trying to operate without certain resources. DR&BC deals with processes, monitoring, alerts, and plans that help organizations prepare for keeping business vital systems online during and after a disaster, as well as restarting lost operations and systems.
-
Identity and Access management:
Identity management refers to the frameworks, processes, and activities that enable legitimate individuals to access information systems within an organization. Implementing strong information storage techniques that assure data security at rest and in transit is part of data security.
-
Cloud Security:
Cloud Security includes the practices and tools that protect cloud computing environments from both external and internal cyber threats. It involves prevention from unauthorized access and keeping data, information in public, private and hybrid cloud secure from various threats.
What skills are needed for a job in cyber security?
For working in a job in cyber security, an individual must require to know basic technical skills in network and system administration, operating systems and virtual machines, network, programming skills, digital forensics, data management, and cloud security.
For personal or soft skills an individual requires to have an analytical thinking and problem-solving mindset, as well in researching, management skills, and communication skills. Mixing knowledge of technical skills and soft skills is required in cybersecurity.
To become a cybersecurity professional one must have a degree in IT security or Computer Science. Courses on cyber security like CEH, CISSP, and CISA have equivalency with the IT degree mentioned above. The certificates of completion of these courses or a degree are required to become a cybersecurity professional. Becoming a cybersecurity professional an individual must have a wider and broader concept of IT security, basic knowledge of Computer Science, and various personal and technical skills.
What is the Scope of Cybersecurity in Nepal?
Due to recent threats in many financial institutions and digitization, cybersecurity is alarmingly increasing. In the Global Cybersecurity Index, Nepal is ranked 94th. With the rise of various Cyber Security company in Nepal such as Eminence ways, Vairav Tech, Bugv, Cynical Technology. Cybersecurity in Nepal has been adopted by numerous FinTech businesses, the Nepali telecom authority, organizations, and commercial banks. As a result, Cybersecurity degree in Nepal has emerged as one of the most sought field in tech.
Cybersecurity specialists are in great demand all over the world. Both the public and private sectors are prone to cyber-attacks. The need of the digital world today requires cyber security to defend against cyber-attacks.
But Nepal also struggles with a general lack of appropriate IT policies, programs to raise security awareness, and knowledge of new technologies, which has led to a lot of spamming, phishing, and password piracy issues.
Find out everything about BSc IT in Nepal at islington college
Some job roles in Cybersecurity in Nepal are:
Cybersecurity specialist:
An authority in the field of information technology security is a "cyber security
specialist." They are responsible for safeguarding the software development
process. They protect networks from outside threats like hackers who want access
for unlawful purposes.
Information security analyst:
To secure computer networks, information security analysts install software like
firewalls. They develop and implement security measures to safeguard a
company's computer networks and systems.
Penetration tester:
Penetration tester helps organizations in locating and addressing security flaws
that affect their digital assets and computer networks.
Network security engineer:
Network security safeguards your network and data against breaches, privacy
violations, and other threats. This is a broad and all-encompassing term that
refers to processes, rules, and configurations relating to network use, accessibility,
and overall threat protection, as well as hardware and software solutions.
Software security engineer:
Software security engineering tests services, processes, techniques, and tools to
figure out any security-related issues.

